Decrypting Cordova "Crypt File" plugin
Introduction
While doing my daily job, I found an interesting android mobile application. It’s a hybrid mobile application, written using Cordova.
Cordova in a nutshell:
“Apache Cordova is an open-source mobile development framework. It allows you to use standard web technologies - HTML5, CSS3, and JavaScript for cross-platform development. Applications execute within wrappers targeted to each platform, and rely on standards-compliant API bindings to access each device’s capabilities such as sensors, data, network status, etc.”
Reference: https://cordova.apache.org/docs/en/latest/guide/overview/
As usual I start with static analysis by “decompiling” the application using “apktool”, and browse to “assets/www” folder, this is where all HTML/CSS/JS file for Cordova located.
What’s make this application interesting is, all the files is encrypted.
Analysis
Analyzing the application, it turned out that it is using Cordova plugin called “crypt file” (https://github.com/tkyaji/cordova-plugin-crypt-file)
I have made a decryptor in order to ease static analysis. I have also made a encryptor for application recompilation during analysis. Example for patching the SSL Pinning/Root Detection mechanism.
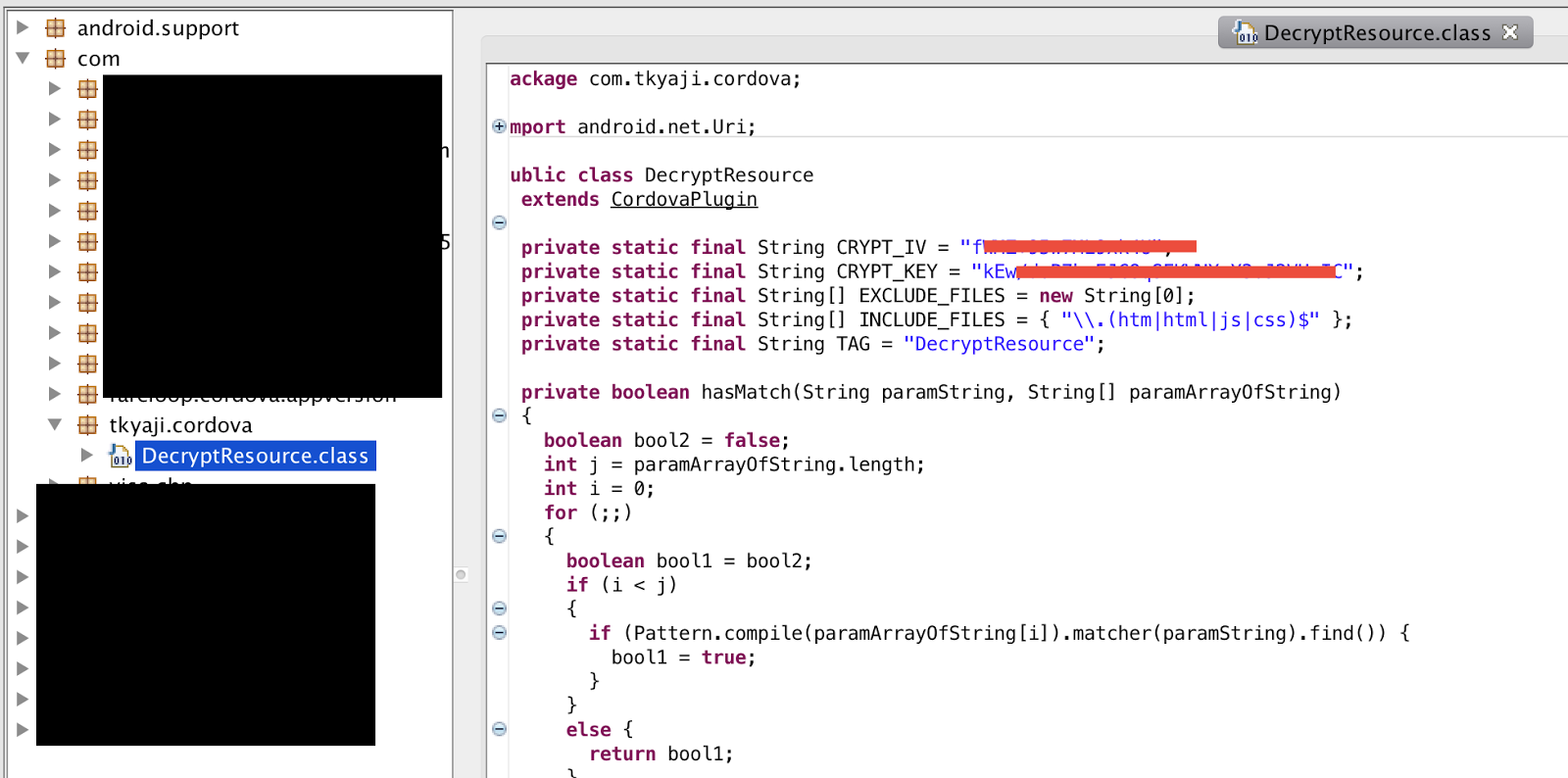
In order to use the tool, first you need to retrieve the KEY and IV from the application. It not complicated as the KEY and IV is located at com.tkyaki.cordova.DecryptResource.class
And finally this is the tool, written in nodejs.
Decryption Tool
update config.key and config.iv accordingly